Safeguard your fleet, fortify your cybersecurity
External Attack Surface Management
EASM is the service that protects the digital assets and entry points of an organization that are exposed to the public Internet. These entry points, collectively known as the external attack surface, include any IT infrastructure, applications, systems, and services that could potentially be targeted by attackers. A few examples are potentiall vulnerabilties, dataleaks (password breaches), server misconfigurations.
Key components
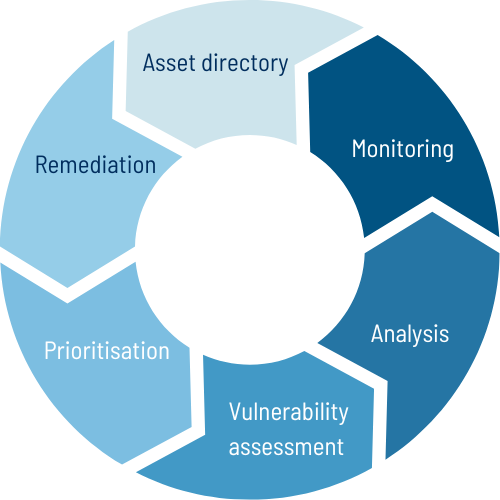
Automatically identify all internet-exposed assets, from vessel networks to remote management systems, creating a real-time inventory of your digital footprint.
Detect weak points in your infrastructure, such as unpatched software, outdated protocols, or misconfigurations, that hackers could exploit.
Stay ahead of cybercriminals with actionable insights from global threat feeds and specific data sources gathered by our inhouse cyber experts.
Proactively track potential entry points and emerging risks 24/7 to prevent breaches before they occur.
Get expert guidance on mitigating attacks, from domain misconfiguration to explanation of breaches or potentiall vulnerabilities. With EASM you have an automated team monitoring your companies attacks surface 24/7.

6 stages of EASM