The ultimate defense from within
NETWORK DETECTION & RESPONSE
Network Detection and Response (NDR) is a security solution used to detect and prevent malicious network activity, investigate and perform forensics to determine root cause, and then respond and mitigate. Therereby protecting organizations against cyber threats.
Implementing NDR will give organizations greater visibility into what is actually on the network as well as all activities. In turn, this will enable security teams to identify and stop suspicious network activity rapidly and minimize its impact on a daily business.
Port-IT NDR silently monitors the vessels network, watching for malicious events or suspicious traffic, even between devices only used internally, such as the VDR and a guest PC. Once this kind of traffic is detected the solution will deploy forensics, mitigate the issue and instantly informs the Port-IT Security Operations Center (SOC) team.
To detect malicious kinds of traffic it uses a combination of artificial intelligence, machine learning and userdefined policies, offering intelligent layers on which the configuration can be strengthened.
Port-IT NDR uses NTA, Network Traffic Analysis. NTA does not only monitor the network perimeter, but more importantly all traffic within the network for complete coverage. NDR detects threats across the entire network, including BYOD & IoT devices and even advanced unknown attacks that other solutions have missed.
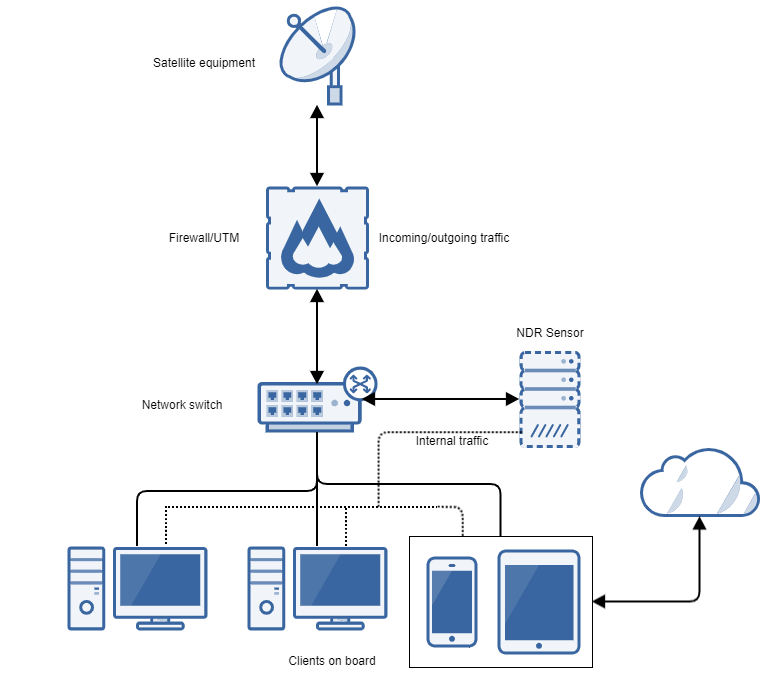
Example of a local network detection
What is NDR?



