Minimize security risks onboard your vessel with a Vulnerability Management plan
Naval Wolf
The maritime industry is facing unique challenges in safeguarding its digital infrastructure. Hackers are always on the lookout for weaknesses in computer systems onboard, patiently waiting for opportunities to exploit those weaknesses and attack. Vulnerability management is used in both IT and OT environments. Our service is hosted in a single pane of glass with our other security services enabling customers having full control over all their security services via a single portal.
A vulnerability is a security loophole or weakness in an organization’s system, application, or network that can be exploited by attackers to gain unauthorized access. Examples of vulnerabilities include:
- Unpatched software
- Weak passwords (standard passwords)
- Misconfigured settings
- Use of outdated hardware or software
- Single-factor authentication
- Poor firewall configurations
- Phishing attacks
- Outdated antivirus and spyware definitions
- Incorrectly configured firewalls
Attackers can exploit these weaknesses to gain access to sensitive data, install malware and ransomware on systems, or even shut down networks entirely.
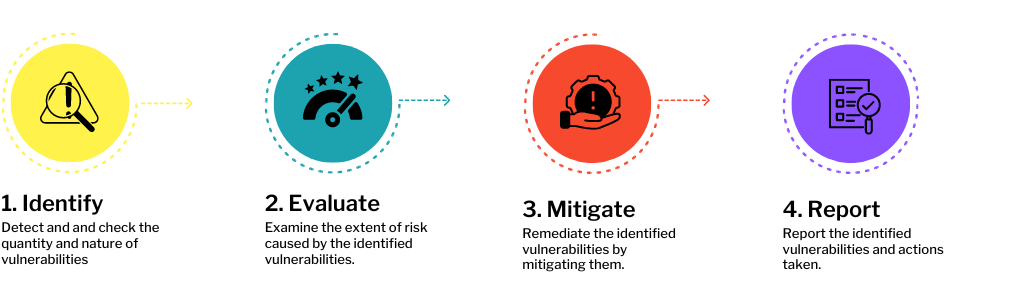
In order to keep the systems safely connected, it’s vital to have a vulnerability management plan in place to manage any weaknesses or vulnerabilities. This strategy helps you identify, evaluate, mitigate and report the risks which could lead to exploits or cyber attacks.

What is Vulnerability Management?
Comply with IACS E26/E27